Unmasking Clickjacking: Stay Informed, Stay Protected
Ayush Goti
Mar 15, 2024
•
5 Min
Ayush Goti
Mar 15, 2024
•
5 Min
TABLE OF CONTENTS
Share
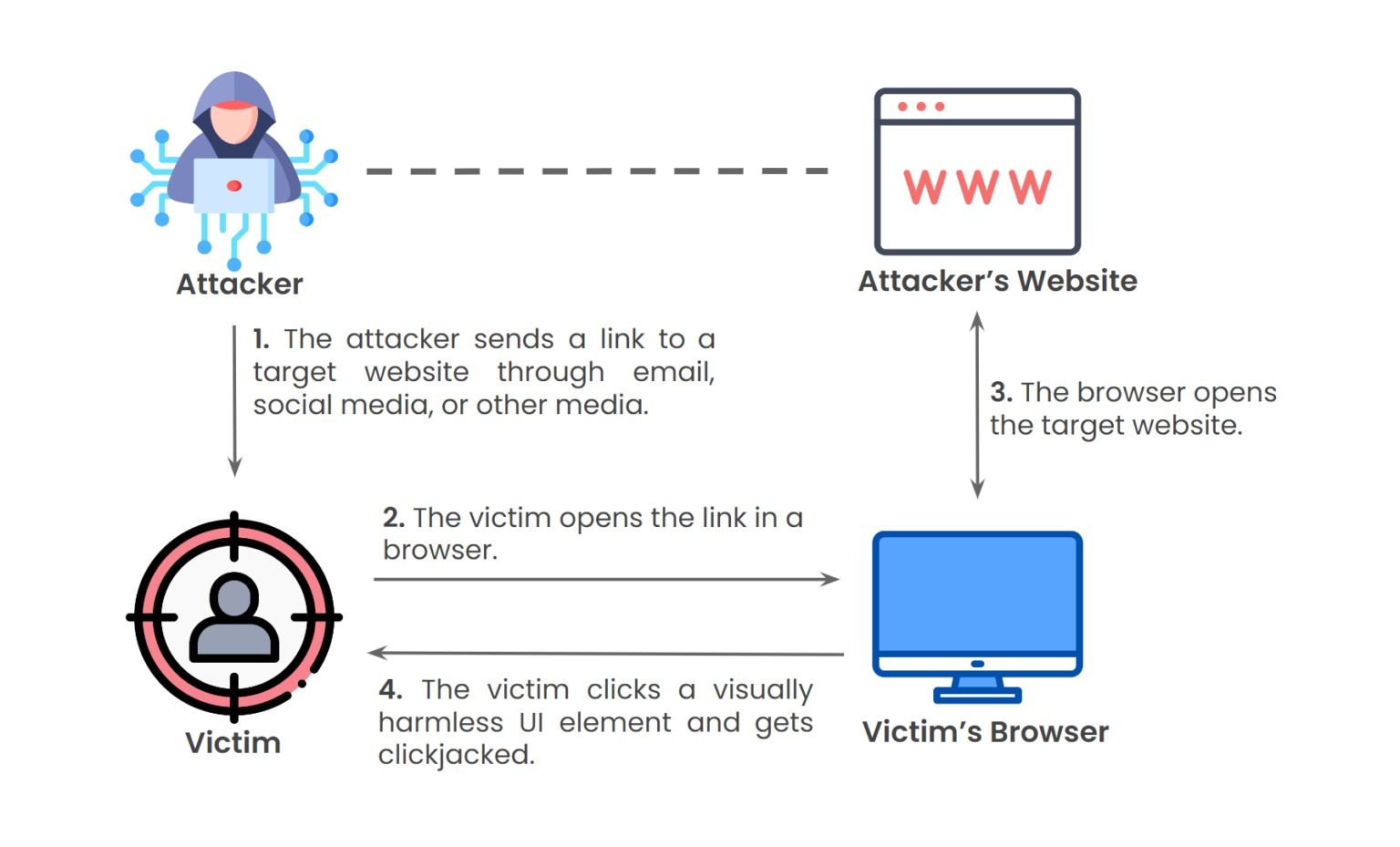
Clickjacking is a sneaky technique used by cybercriminals to trick you into clicking on something without realizing it. Imagine you’re browsing a website and you see a button that looks harmless, like “Play” or “Download.” But behind the scenes, there’s another hidden button or link that the attacker want you to click on, maybe to install malware or give away your personal info, Clickjacking, also known as a “UI redress attack”.

Clickjacking works by tricking you into clicking on something without knowing it. Here’s how they do it,
Clickjacking attacks can do more than hijack cursor clicks. They can also be used to capture information, steal money, invade user privacy, and more, such as
Here we are ending of this blog but “Remember, this knowledge is your best defense against clickjacking. Stay vigilant, stay informed, and keep clicking wisely. Together, we can make the web a safer place for all. Happy surfing, and may your clicks always lead you exactly where you intend them to go.”
“Stay safe online, friends. Keep your clicks sharp and your instincts sharper. Until next time, happy browsing!”
Share